Each user who frequently accesses a multiple-user server over the network needs a user account. This account contains information about the user, such as name and password, and all permissions regulating the user’s network access. It can be set up locally on the terminal server or centrally in a domain using Active Directory.
Users who have similar functions or need the same resources can be grouped. Grouping makes management and assigning privileges easier because functions are no longer tied to individual users. Instead, they can be assigned to the entire group of users.
Local users and groups are managed in a Computer Administration snap-in under the Start\Programs\Administration menu. A user account is always based on data such as the unique name, password, group membership, basic directory, user profile, or logon script. Additionally, there are user properties that have the attribute true (= yes) or false (= no), which are needed, for example, to specify if the user needs to change his or her password on the next logon or if the account is deactivated.
Each user account is defined throughout the system by a security identifier (SID). The SID is generated by an algorithm and is based on the network adapter’s hardware address and the current system time. As such, it is globally unique and remains actively linked to certain objects (for example, files) as security information if a user account is deleted. If a user account is created, deleted, and then re-created using the same name, the new user account does not have the same rights as the old one because it has a new SID.
Managing users and groups is essential for smooth operation both on individual terminal servers and within a domain. Only an administrator or a member of the Account Operators user group has the permissions needed to create new users or modify data of existing users.
The properties dialog box for local users on a terminal server contains tabs for configuring multiple-user options. The following sections give details on each tab.
The Member Of tab is needed to add a user to the Remote Desktop Users group. Only members of this group have permission to access the server via a Terminal Services client.
Use the following procedure to add a user to the Remote Desktop Users group:
Click Add... in the Member Of tab.
Click Advanced... in the first Select Groups dialog box.
Click Find Now in the second Select Groups dialog box.
Select Remote Desktop User from the search results, and click OK.
The Environment tab is used to configure the Terminal Services startup environment for executing an initial program and connecting client devices.
To configure a program, you enter the path to the executable (for example, C:\Program\Microsoft Office\Excel.exe) and an optional start directory (for example, C:\User) for the application data. The program, which starts when the user logs on, becomes an alternative display to the normal Windows 2000 user interface.
The client device connections apply to the existing drives and printers. If required, they can be blended with the existing terminal server resources. In this way, the terminal server can use the printer that is physically attached to the client device as its default printer.
Similar settings can be selected for Terminal Services configuration (described in Chapter 2) and Terminal Services clients (described in Chapter 3). The local user administration settings override the client settings but have a lower priority than the Terminal Services configuration settings.
Time limits for Terminal Services and reconnection settings are entered under the Sessions tab.
Time limits define the maximum duration of certain activities. The time period you choose is completely optional; however, the drop-down menu suggests the following discrete values: Never, 1 minute, 5 minutes, 10 minutes, 15 minutes, 30 minutes, 1 hour, 2 hours, 3 hours, 1 day, and 2 days.
End a disconnected session This time limit specifies the period that a disconnected session is stored in terminal server memory. The user can reconnect to the session within that period of time. A session can be disconnected for many reasons: active session limit, idle session limit, interrupted modem connection, network failure, switching off the client, or selecting the Disconnect option on a Terminal Services client.
Active session limit Here you enter the period after which a client is disconnected from the terminal server or the active session ends. Measurement begins on connection and is not affected by any other limits (for example, idle session limit).
Idle session limit This time limit defines when a session is disconnected or ended if the user has been completely inactive, that is, has not touched the mouse or keyboard for the entire session.
Select the Disconnect from session or the End session radio button to determine what happens when a session limit is reached or the network connection is broken. Users may reconnect to a disconnected session still stored on the terminal server as selected in the From any client or From originating client only radio button. The corresponding protocol must support this property; RDP 5.2 does not (but Citrix ICA does). This option is only supported if you install Citrix MetaFrame XP Presentation Server as described in Chapter 9.
It is possible to overwrite the properties in this tab with different corresponding parameters under Terminal Services configuration and Active Directory settings.
Remote Control is an interesting option for the support of terminal server users. This function is often referred to as mirroring and redirects a user session to another client. As soon as an authorized user can interact with the mirrored session, the function is referred to as remote assistance.
The remote control and remote assistance concepts represent, of course, a major encroachment on the Windows Server 2003 security concept. In some countries, the law forbids mirroring without the user’s knowledge or consent. Additionally, legal regulations might require that the user being observed receive continuous notification for the duration of the mirrored session. For this reason, remote assistance can be disabled for a user account. At a minimum, you should always ask the user for permission to mirror his or her session. If you activate the corresponding remote assistance option, a dialog box is displayed that notifies the user of the administrator’s need and requests the user’s permission. If the user denies permission, the user session cannot be mirrored.
During remote assistance, there are two basic options for the administrator’s level of control in the user session: the administrator can simply view the session or may interact with the session using the mouse and keyboard. These options can be set individually for each user account.
These options can also be set under Terminal Services configuration or Active Directory Group Policies, where they have higher priority.
The Terminal Services Profile tab allows you to assign a special user profile for logging on over a client session. Notice that the Terminal Services profile depends to a certain extent on the user’s default profile.
If only a default profile (Profile tab) is defined, it is valid regardless of where the user logs on (workstation or Terminal Services client).
If only a Terminal Services profile is defined, it applies only if the user logs on through a client session (that is, by using the multiple-user option of a terminal server).
If both default and Terminal Services profiles are defined, the user receives different profiles depending on the user’s client type. The user is assigned a default profile for a normal logon under Windows 2000 Workstation or Windows XP and a Terminal Services profile for logon through a Terminal Services client.
This tab also allows you to assign each Terminal Services user a home folder, which is used only when logging on to a terminal server. It is also possible to revoke a user’s logon privileges to a terminal server, which renders all his or her other configured multiple-user options useless.
Home folders are usually created on file servers that are subject to relatively simple rules. First, the file server must have enough memory to meet the users’ requirements. Second, good data-access and network-connection speed are essential. Finally, file servers need to be as fail-safe as possible. Therefore, they are often configured as cluster systems to ensure the highest availability.
As already described in Chapter 3, the options for connecting terminal servers to their clients are flexible rather than fixed, to adjust to certain general conditions. The corresponding settings can be selected in not just one, but in several different places, each with its own focus.
System-wide settings are defined under Group Policies; these settings override all others.
Connection-specific settings on the terminal server are defined using the Terminal Services configuration tool. These settings have a lower priority than Group Policies, provided they can also be modified there.
User-specific settings are defined through user accounts; these settings have a lower priority than Group Policies and Terminal Services configuration.
Client-specific settings are defined on Terminal Services clients (for example, through a remote desktop connection under Windows XP). These settings have the lowest priority.
However, not all connection options can be changed everywhere. To determine exactly where to configure certain properties, consult the following table, which compares Terminal Services configuration, user accounts, and remote desktop connection.
|
Option |
Terminal Services Configuration |
User Account |
Remote Desktop Connection |
|---|---|---|---|
|
Configure the LAN adapters used |
Yes |
No |
No |
|
Set a counter for maximum connections per LAN adapter |
Yes |
No |
No |
|
Select encryption level |
Yes |
No |
Preset |
|
Enable automatic logon |
Yes |
No |
Yes |
|
Always request password |
Yes |
No |
No |
|
Time limits for connections |
Yes |
Yes |
No |
|
Time limit for disconnected sessions |
Yes |
Yes |
No |
|
Idle session limits |
Yes |
Yes |
No |
|
Handle interrupted connections |
Yes |
No |
No |
|
Start initial program |
Yes |
Yes |
Yes |
|
Redirect local drives |
Yes (nonbinding) |
Yes |
Yes |
|
Redirect local printers |
Yes (nonbinding) |
Yes |
Yes |
|
Redirect local serial ports |
Yes (nonbinding) |
No |
Yes |
|
Redirect local clipboard |
Yes |
No |
No |
|
Redirect local audio streams |
Yes |
No |
No |
|
Predefine/select desktop size |
No |
No |
Yes |
|
Predefine/select color depth |
Yes |
No |
Yes |
|
Connect to the console |
No |
No |
Depends |
|
Automatic reconnection |
No |
No |
Yes |
|
Control network bandwidth |
Yes |
No |
Yes |
|
Control full-screen options |
No |
No |
Yes |
|
Activate remote desktop |
Yes |
Yes |
No |
|
Define Terminal Services user profile |
No |
Yes |
No |
|
Define Terminal Services home folders |
No |
Yes |
No |
|
Logs |
Yes |
No |
No |
A terminal server is rarely set up in isolation, and a corporate network is not built around new terminal servers. Normally, new servers are integrated into already existing and established network structures. This next section deals with domain integration and Group Policies for terminal servers.
Once they reach a certain size, computer environments based on Windows 2000 and Windows Server 2003 are usually organized into domains. A domain on a terminal server functions primarily as central instance for authenticating users and assigning shared printer and file resources. Together with the domains, Active Directory is the directory service for Windows 2000 and Windows Server 2003. It saves information on network objects, such as users, groups, servers, or printers. Users and administrators can call up this data using simple search functions. The Active Directory service uses a structured data memory on which the logical and hierarchical order of directory information is based.
| Note |
This book does not explore in detail the complex design objectives and models of domains and the Active Directory service. However, we cannot ignore these topics completely. We will indeed examine them, always in the context of terminal servers. |
In principle, a terminal server within a domain behaves just like a “normal” system running Windows 2000 Professional or Windows XP. The only difference is that one computer name is valid for multiple users. Therefore, a terminal server is integrated into a domain structure normally, that is, by using the System Properties window accessed through Control Panel. Within the System Properties window you select the file tab Computer Name and change the membership to a domain or working group by using the Change... button.
The More... button opens another dialog box in which you can add a suffix to the DNS name and see the NetBIOS computer name. The NetBIOS computer name is used for interoperability of older computers and services.
A terminal server should never assume the function of a domain controller. The Terminal Services design objective is clearly to provide optimally performing applications to interactive users. This, of course, strongly contradicts the highly prioritized processes needed for database synchronization and preferred handling of logon requests. Therefore, we recommend using at least two dedicated domain controllers.
Under Microsoft Windows NT 4.0, the Group Policy Editor was introduced. With the help of this editor, system policies could be created to manage the work environment and user actions. These policies were also used to enforce system configuration settings for all computers under Windows NT 4.0. This concept was significantly enhanced under Windows 2000 through the introduction of Active Directory. Many familiar tools were standardized and replaced by the new Active Directory integrated Group Policy tools and the attendant extensions. Windows 2000 offered other completely new functions, such as setting policies at different locations and predefining the scope of policies through security groups. For an administrator, Group Policy has been one of the most important enhancements in the Windows network management environment.
If computers and user accounts under Windows Server 2003 are combined within domains and organizational units, their properties and restrictions are controlled via Group Policies. Group Policy is a great tool for fine-tuning a Windows Server 2003 network environment and its computers. This especially applies to user interface functions, software installation, administrative templates, redirecting access to folders, security settings, Microsoft Internet Explorer administration, as well as Terminal Services configuration and terminal server session administration. However, bear in mind that problems are inherent in mixed terminal server environments running different Windows versions with a common Group Policy.
Basically, Group Policies can be applied to user or computer objects within sites, domains, or organizational units. Computer objects are not limited to client computers, but can also include domain controllers and all servers (Windows 2000 Server and Windows Server 2003) in a domain. Settings are passed from one Active Directory level to the underlying levels if not expressly prohibited. At a minimum, you can even configure a standalone server through Group Policies. This is known as a local group policy.
Group Policies is a powerful administrative tool for Windows Server 2003. We will encounter it often in this book.
| Note |
To invoke the tool for managing the Group Policy on a domain controller, select Administration\Active Directory Users and Computers. Use the Gpedit.msc command to open the local group policy object on a stand- alone terminal server. To differentiate the options for the various operating systems, you can filter the administrative template policies by various criteria under View\Filtering.... |
With Group Policies and the corresponding expansions, you can perform the following tasks essential to terminal servers:
Policy administration A file is generated for Group Policies that contains registry settings. These settings are written to the registry database in the area for individual users or local computers. The entries in the registry database determine system behavior for users or the computer. (See also Chapter 6.)
Script assignment Executing scripts to boot up and shut down the computer and log users on and off. It is possible to enter several scripts to be executed in a predefined sequence. In so doing, however, you might disable scripts that were set in user configuration. It is therefore not possible to combine both script configurations.
Directory redirection The Application Data, Desktop, My Documents, My Pictures, and Start Menu directories on a local computer can be moved to one network resource.
Application management Assigning, publishing, updating, and repairing applications, which requires an additional expansion of the software installation. However, please make sure that you really want to distribute software from a terminal server. Performance bottlenecks are likely to occur due to the potentially large number of simultaneous users who can be assigned software.
Security options Override local security settings with centrally managed policies.
A Group Policy always consists of two parts, user configuration and computer configuration. They represent two different categories of configuration. If needed, you can set an object within Active Directory to only load one of the two parts. This is useful if the other part is not relevant for the object and optimizes the communication effort on loading the Group Policy.
As you can see, users and computers are the only types of Active Directory objects that contain policies. Policies are not used with security groups, in particular. For performance reasons, security groups filter the policies through Accept Group Policy for access control. This entry can have the value Enabled or Disabled or is not configured at all. (See also Chapter 8.)
Policies can thus be set locally and centrally. But which setting takes precedence if there are different values for one property? There is a clear hierarchy in applying Group Policies.
Local Group Policy object Exactly one group policy object is saved locally on each Windows Server 2003. This object can be found under %SystemRoot%System32\GroupPolicy.
Site (Location) In the next step, all Group Policy objects assigned to one Site are processed. This process follows the sequence defined by the administrator. A site is defined within Active Directory by the Administrator and allows definition of synchronization between sites and local logon rules.
Domain Several Group Policy objects assigned to one domain are processed in the sequence defined by the administrator.
Organizational units Organizational units can be nested within other organizational units, and an object (computer or user) may only exist in one organizational unit. Thus, rules defined within Group Policy at the top level of the Active Directory organizational unit hierarchy are applied first. Then the Group Policy rules in the subordinate levels are applied, until finally those Group Policy levels that contain the users or computers objects are processed.
If policies differ, the policies applied at a later point in time overwrite the previous ones by default. If there are no differences in the settings, both previous and later policies are followed.
A computer configuration is applied to a computer on startup, regardless of who logs on. Computer configuration is divided into the following basic extensions, which can be further delineated:
Software Settings Computer-specific settings for the software installed through Group Policy.
Windows Settings Scripts for startup, shut-down, and security settings.
Administrative Templates Windows components, system, network, and printer.
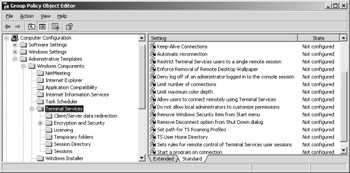
Figure 4-30: Setting computer-specific Group Policies for Terminal Services.
The following list specifies the key locations where the computer configuration can be adapted for terminal servers.
Computer Configuration\Windows Settings\Security\Local Policies\User Rights Assignment This comprises numerous settings, including an option to allow or prohibit individual user groups from logging on through Terminal Services. For this reason, this configuration is essential for terminal servers.
Computer Configuration\Windows Settings\Security\Local Policies\Audit Policy Settings for logged system events.
Computer Configuration\Windows Settings\Security\Local Policies\Security Options Security Settings for domains, connected devices, interactive logon, network, system objects, and monitoring. One of the settings relevant to terminal servers is whether users may install printer drivers or not.
Computer Configuration\Windows Settings\Security Settings\Software Restriction Policies Central definition for application options of installed software.
Computer Configuration\Administrative Templates\Windows Components\Application Compatibility Options to enable and disable mechanisms related to application compatibility and handling 16-bit applications. The settings you select here might limit the use of a terminal server (for instance, if it can no longer execute 16-bit applications).
Computer Configuration\Administrative Templates\Windows Components\Terminal Services General Terminal Services parameters, to some degree similar to the ones definable in Terminal Services configuration or user accounts.
Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Client/Server Data Redirection Configure device and port redirections because they can also be defined under Terminal Services configuration, user administration, or a terminal services client.
Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Encryption and Security Select parameters for password entry, RDP encryption, and RPC security.
Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Licensing Settings for licensing over license servers and license updates for terminal servers and Terminal Services clients.
Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Temporary Folders Using temporary folders per session and deleting temporary folders when a user session on a terminal server ends.
Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Session Directory System behavior when using a session directory (starting with Windows Server 2003 Enterprise Edition only).
Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Sessions Configure time limits just like under Terminal Services configuration and user administration. If the settings also apply to user configuration, computer configuration has priority in case of conflict.
Computer Configuration\Administrative Templates\Windows Components\Windows Installer Configure installation environment; if at all possible, prohibit uncontrolled installations by users for terminal servers. You also decide if administrators may perform installations from Terminal Services sessions.
Computer Configuration\Administrative Templates\Windows Components\Windows Update Settings for automatic system updates, which must be very restrictive for many terminal server environments. These settings prevent unsynchronized system updates that could cause inconsistent conditions in server farms.
Computer Configuration\Administrative Templates\System\User Profiles System settings for user profiles. Contains time limits for centrally saved profiles and options for local, cached profiles. These parameters are essential for terminal servers that are organized in farms.
Computer Configuration\Administrative Templates\System\Scripts Configure waiting times, synchronization conditions, and visibility of system-relevant scripts (for example, logon script or start script). Because logon scripts often a play key role on terminal servers, the settings you select here are very important. If the settings also apply to user configuration, computer configuration has priority in case of conflict.
Computer Configuration\Administrative Templates\System\Logon Among other options, choose to execute certain programs when a user logs on or process the usual lists. Initialization of customer-specific applications for terminal servers can depend on these settings.
Computer Configuration\Administrative Templates\System\Group Policies Settings that influence the behavior of Group Policies updates on affected computers and which policies apply.
Computer Configuration\Administrative Templates\System\Remote Assistance Basic settings for remote assistance options based on Terminal Services.
Computer Configuration\Administrative Templates\Printers Settings on printer use and setup.
Many of the above configuration elements are described in much more detail later in this book.
A user configuration is applied to a user at logon, regardless of where the user logs on. It is divided into the following basic extensions, which can be delineated in even greater detail:
Software Settings User-specific settings for the software installed.
Windows SettingsRemote installation services, logon and logoff scripts, security settings, and Internet Explorer maintenance.
Administrative Templates Windows components, start menu and taskbar, desktop, Control Panel, released folders, network, and system.
The computer configuration has priority over the user configuration where the options are the same.
The following list specifies the key locations where the user configuration can be adapted for terminal servers:
User Configuration\Windows Settings\Scripts Select scripts to be executed upon user logon and logoff. Logon and logoff scripts are critical for smooth operation of a terminal server environment.
User Configuration\Administrative Templates\Windows Components\Application Compatibility Option to prevent user access to 16-bit applications.
User Configuration\Administrative Templates\Windows Components\Windows Explorer Numerous options for Windows Explorer settings. Restricting them can significantly improve terminal server security.
User Configuration\Administrative Templates\Windows Components\Terminal Services Select a program that is automatically executed when a user session is established and determine remote monitoring settings.
User Configuration\Administrative Templates\Windows Components\Terminal Services\Sessions Configure time limits just like under Terminal Services configuration and user administration.
User Configuration\Administrative Templates\Windows Components\Windows Update Eliminate access to all Windows Update functions. This prevents users from modifying the terminal server configuration.
User Configuration\Administrative Templates\Start Menu and Taskbar Comprehensive configuration options for start menu items and taskbar elements to control user access.
User Configuration\Administrative Templates\Desktop Modify desktop icons and context menu items. Additional settings for Microsoft Active Desktop and user access to the Active Directory service.
User Configuration\Administrative Templates\Control Panel Control access to the entire Control Panel and some individual tools. Prevent installation of new software or printers or set standards for desktop design. These options help improve terminal server stability.
User Configuration\Administrative Templates\System\User Profiles Link a user’s home directory with the root of a share, set profile size, or exclude directories from profiles saved on a server.
User Configuration\Administrative Templates\System\Scripts Configure synchronization conditions and logon script visibility. Because logon scripts often play a key role for user sessions on terminal servers, the settings you select here are very important.
User Configuration\Administrative Templates\System\Logon Choose to execute certain programs when a user logs on or process the usual lists.
User Configuration\Administrative Templates\System\Group Policies Settings that influence the behavior of Group Policies updates for affected users and which policies apply.
Many of the above configuration elements are described in much more detail later in this book.
| Tip |
All relevant User Configuration files are located on the server in the %Systemroot%\system32\GroupPolicy\User folder. The folder contains the Registry.pol file with the selected user-specific settings of the administrative templates that are taken directly from the Group Policies Editor. You can also save script files here that are executed when a user logs on or off. |
Group Policies is an excellent tool for managing multiple terminal servers within Active Directory. It manages users and groups in the predefined Users container. There is a separate container for the computers, including the corresponding settings. However, terminal servers can also be bundled into individual organizational units, each with its own Group Policies. In principle, an Active Directory object (for example, a computer, a user, or a group) can be in only one container or organizational unit.
When implementing Group Policies on terminal servers, keep the following in mind: Usually, terminal servers are combined into one organizational unit to enable uniform configuration using Group Policy. User settings should definitely be defined as well. However, as already mentioned, the settings apply only to objects that are part of the related organizational unit. User settings for accounts in other organizational units are therefore not carried over.
To solve this problem, there is a very important setting under Computer Configuration\Administrative Templates\System\Group Policies: Loopback Processing Mode for User Group Policy. Here you can activate the User Configuration that is part of the organizational unit for the server in question. If a user logs on to the server, the settings of his or her organizational unit will be replaced by or combined with the user settings of the server’s organizational unit. If they are combined, the user settings in the server’s Group Policies take precedence over the normal user settings in conflict situations.
Here is a practical example of this mechanism: users who work in a company’s subsidiary have local, conventional clients running Windows XP with their Internet Explorer proxy settings pointing to the subsidiary’s proxy server. If the users log on to a terminal server located at headquarters, the headquarters’ proxy server should be used. This can be configured using the loopback processing mode.
So how can multiple terminal servers within one domain be made available to a user group?
Install the terminal servers and add them to a domain.
On one of the corresponding domain controllers, create a new global group for the terminal server users in the Users container of the Active Directory Users and Groups tool. The group should have a meaningful name, such as WTS users.
Add the newly created or existing user accounts in the Users container to the new group of terminal server users.
Create a new organizational unit for the terminal servers in the domain, named, for instance, Terminal Servers. Add all involved terminal servers to this organizational unit. The organizational unit receives a new Group Policy object for which you activate the loopback processing mode (preferably using Replace). At this level, you can also define any additional Group Policies for terminal servers.
On each terminal server, add the global terminal server user group you created to the local Remote desktop users default group.
Now all users in the global terminal server user group can log on to all terminal servers in the corresponding organizational unit.