|
|
< Day Day Up > |
|
8.1 Intrusion Prevention StrategiesSeveral intrusion detection strategies have been developed, including:
Figure 8-1 is Snort running as a session interceptor using the flexible response plug-in. When an attack is detected, RST packets are sent to the hosts, ending the conversation. Figure 8-1. Snort as a session interceptor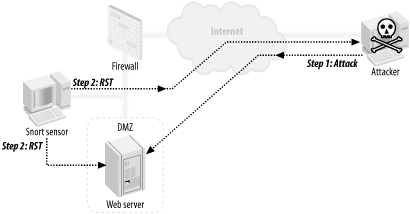 Figure 8-2 shows Snort running as firewall/router/IPS. When an attack is detected, all future traffic from the attacker is blocked. Figure 8-2. Snort as a gateway IPS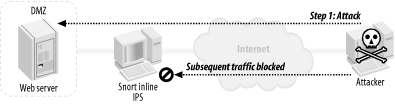 Figure 8-3 shows Snort running with SnortSAM. Figure 8-3. Snort managing access lists on border devices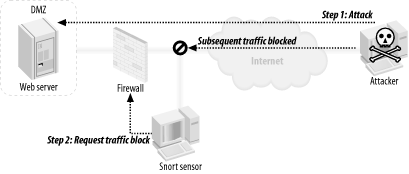 When an attack is detected, the border router is directed to block inbound traffic from the attacking host. |
|
|
< Day Day Up > |
|