|
|
< Day Day Up > |
|
2.2 Dissecting a Network PacketA network packet is nothing more than a chunk of data that an application wants to deliver to another system on the network. This chunk of data has information added to the front and back that contains instructions for where the data needs to go and what the destination system should do with it once it arrives. The addition of this routing and usage information is called encapsulation. The TCP/IP model uses four layers of encapsulation, also referred to as a stack or an IP stack. A packet is something like Russian Matroishka or "nesting" dolls: painted wooden figurines that hold smaller versions of themselves. Each doll is slightly smaller than the parent into which it is placed. The smallest doll, which cannot be opened, is the actual application data. Each larger, enclosing doll represents the header data affixed to the original content. The insertion and removal of each layer of a Matroishka doll is equal to a network-level header being added or removed from a packet. Figure 2-2 illustrates the process. We start with a chunk of application data, to which we add a header. We take that data (application data plus application header) and package it up as a series of TCP segments by adding TCP headers. We then add an IP header to each TCP segment, making IP datagrams. Finally, we add Ethernet headers and trailers to the IP datagrams, making an Ethernet frame that we can send over the wire. Each layer has its own function: TCP (the transport layer) makes sure data gets from point A to point B reliably and in order; IP (the network layer) handles routing, based on IP addresses and should be familiar to you; and Ethernet (the link layer) adds low-level MAC (media access control) addresses that specify actual physical devices. It's also important to note that there are several choices at each layer of the model: at the transport layer, you can see either TCP, UDP, or ICMP. Each layer of the network stack is unaware of the layers above and below. The information coming from the layers above are simply treated as data to be encapsulated. Many application protocols can be packed into TCP. When the packet is received at its final destination, the same process is repeated in reverse. The packet is de-encapsulated and the headers stripped off when it is received by the intended target. Figure 2-2. User data is encapsulated with headers from each layer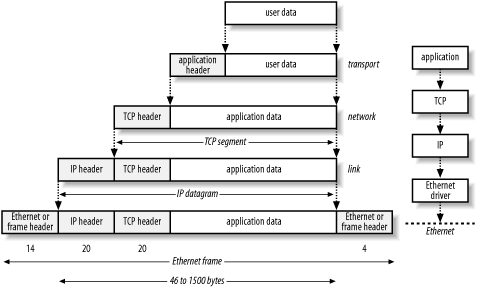 Most alerts generated by Snort are the result of matching strings inside the data payload of the packet, but many others are generated by the headers—most commonly the IP and TCP headers. 2.2.1 The IP HeaderPrimarily, the IP header specifies where the packet is going and where it came from. The IP header (Figure 2-3) is 20 bytes long and contains the following information:
Figure 2-3. The IP header: four bytes per row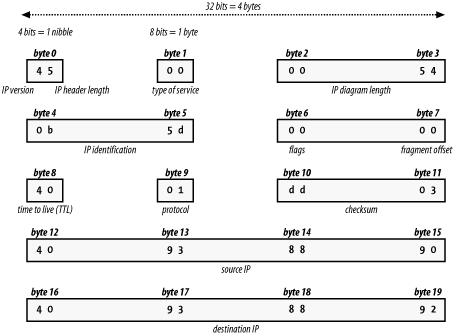 2.2.2 The TCP HeaderThe TCP header is used to inform the receiving machine which upper-layer application should receive the data and information related to the establishment, maintenance, and tear down of TCP connection-oriented conversations. The TCP header (Figure 2-4) is of variable length and contains the following information:
Figure 2-4. The 12 fields of a TCP header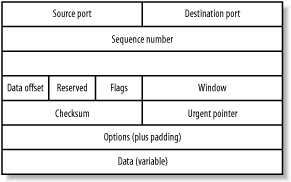 |
|
|
< Day Day Up > |
|