|
|
< Day Day Up > |
|
13.1 Barnyard (and Sguil)One of the costliest activities Snort performs is its alert logging. Data needs to be gathered, formatted, and written. In the case of database writes, Snort must send the alert to the database and wait for confirmation of a successful write. The situation is made even worse when the database server is running on another system on network. Snort has the ability to dump the information that it has gathered on a particular alert into a binary file. This is very quick, since no processing needs to be performed on the data. The Barnyard application reads this file, formats the alert data, and writes it to the chosen output mechanism. The output mechanism can be the conventional Snort logfile, syslogs, comma-separated-value formatted (CSV) file, or a database server. Barnyard can be configured to run on the same platforms as Snort, and their installation and configuration are very similar. Figure 13-1 illustrates the way Snort and Barnyard work together. Barnyard does a very good job of logging to the ACID database allowing Administrators to continue using familiar tools. Figure 13-1. Barnyard working with Snort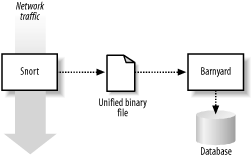 13.1.1 Configuring Snort's Unified Binary OutputWhen using unified binary output, Snort is configured normally; the only difference is the output plug-in selected in the snort.conf file. The log_unified output plug-in is the only output plug-in that should be configured. The format of the directive is: output log_unified: filename <filename>, limit <log file size>
A sample snort.conf entry would be: output log_unified: filename unified.log, limit 512 When Snort starts writing to a new file as a result of the size limit being reached, Barnyard continues processing with new file automatically if it is running in continual mode (see Section 13.1.4 below). 13.1.2 Installing BarnyardDownload Barnyard from http://www.snort.org/dl/barnyard and extract it to a standard location (I prefer /usr/local/src/barnyard). To enable database support, you need to use a directive when running configure. To enable support for MySQL support, use (--enable-mysql); to enable PostgreSQL, use (--enable-postgres). The command line is below: # cd /usr /local/src/barnyard/barnyard-0.x.0/ # ./configure --enable-mysql # make # make install After install, you can find the Barnyard executable in /usr/local/bin and the barnyard.conf file in the /etc directory in your source directory. You can copy this to a location like /usr/local/etc or keep it where it is. 13.1.3 The barnyard.conf FileMost Barnyard options are managed using the barnyard.conf file. There are two sections to the file: the declarations and the output plug-ins. Here are the configuration declarations:
The output plug-ins consist of:
13.1.4 Barnyard Command-Line OptionsBarnyard runs in one of three modes: one-shot, continual, or continual with checkpoint. One-shot mode (or batch mode) is used to run Barnyard against a single unified logfile and then exit. Continual watches a unified logfile as it is written to. The continual with checkpoint mode is similar to the continual mode except it keeps track of where it is in the file by keeping a pointer in a file (sometimes called a waldo file). If Barnyard crashes, processing will continue at this point in the unified logfile. The mode that Barnyard is running in (as well as other potentially ephemeral configuration settings) is designated at the command line. The command line options for Barnyard are:
Here are some sample command lines (they can get very long). First, there's batch (one-shot) mode: barnyard -c /usr/local/etc/barnyard.conf -d /var/log/snort \ -c /usr/local/share/snort_rules/classification.config \ -s /usr/local/share/snort_rules/sid-msg.map \ -g /usr/local/share/snort_rules/gen-msg.map -o unified.log.1083726235 Then we have continual mode with checkpoint: barnyard -c /usr/local/etc/barnyard.conf -d /var/log/snort \ -c /usr/local/share/snort_rules/classification.config \ -s /usr/local/share/snort_rules/sid-msg.map \ -g /usr/local/share/snort_rules/gen-msg.map -w /usr/local/etc/waldo.chk \ -f unified.log 13.1.5 Sguil: An Alternative Management Console
As the prerequisite list indicates, installing Sguil can be hairy. Getting it running involves installing the standard Snort components, Tcl (tool control language) and tk (a graphical user interface toolkit), several add-on Tcl libraries, and the Tcpflow and p0f applications. Then set up a database for Sguil to use, install the GUI server, and the GUI client, patch Snort's source code and recompile, configure Barnyard's Sguil output plugin, and configure a script to get the data from Snort, Tcpflow, and p0f into the database. Detailed installation instructions are available on the Sguil web page. Sguil is a near real-time interface to Snort alerts that relies on Barnyard, Tcpflow, and p0f to gather alert data. Tcpflow and p0f are used to create a transcript of network traffic that can be useful in discrimating false positives and post-incident forensic analysis. The interface is actually very nice to use and presents the alert information in a useful format. An extract from the Sguil home page:
Sguil isn't that different from the ACID interface: both allow you to monitor alerts and search by event, sensor, alert classification, alert priority, or timestamp. Sguil is more up-to-date with the latest preprocessors—particularly the new flow-portscan system. Both ACID and Sguil lack sensor-management tools. Where connecting to ACID is easy since it is a web-based interface, the only way to get a remote client to connect to a central server is by using an exported X-session (a security no-no). Looking back at the last few paragraphs, I see that I'm drawing a lot of comparisons between ACID and sguil. Functionally, they are very similar. Sguil's transcript feature differentiates it. A daunting installation, poor client model, and lack of many new features make it difficult to recommend Sguil. I advise sticking with ACID. Figures Figure 13-2 and Figure 13-3 show screenshots of Sguil in action. Figure 13-2. Sguil console in action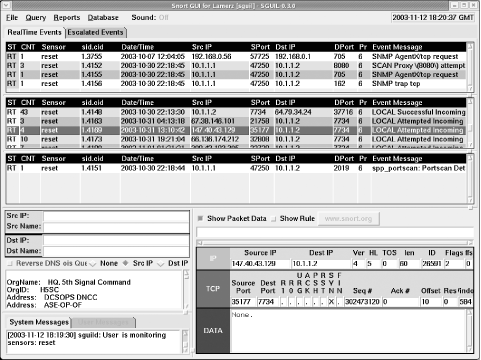 Figure 13-3. The sguil query builder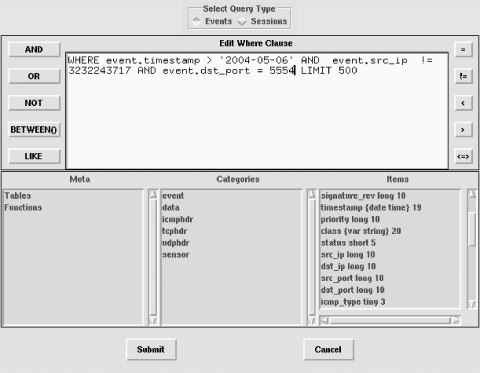 |
|
|
< Day Day Up > |
|