|
|
< Day Day Up > |
|
12.1 Open Source SolutionsMany open source tools are designed to help with some aspect of managing Snort. Most target a particular task (updating rules, managing alerts, and so on), but some are surprisingly full-featured. Snort has changed a great deal (the moves from 1.x to 2.x and from 2.x to 2.1.x were dramatic). Some of the tools do not support new features, such as the new preprocessors (even ACID is showing signs of age as its development falters). 12.1.1 SnortReport
Installation of SnortReport consists of nothing more than ensuring that the prerequisite applications are installed and running, extracting a directory of web pages and PHP files, creating a directory in your web root (or creating a virtual host), and editing the srconf.php file. The srconf.php file is filled out with login information for the MySQL database that your Snort sensors are logging to. The development of SnortReport seems to have been stalled for some time. The current version on the Freshmeat web site is 1.04, but the FreeBSD ports catalog has install source for Version 1.2. SnortReport is nothing more than an interface into the alerts in the database. It is does not have many features, but can be a useful interface for keeping an eye on things. All things considered, ACID is far superior (and not much harder to get running). Figure 12-1 shows the SnortReport main page. Figure 12-1. SnortReport main page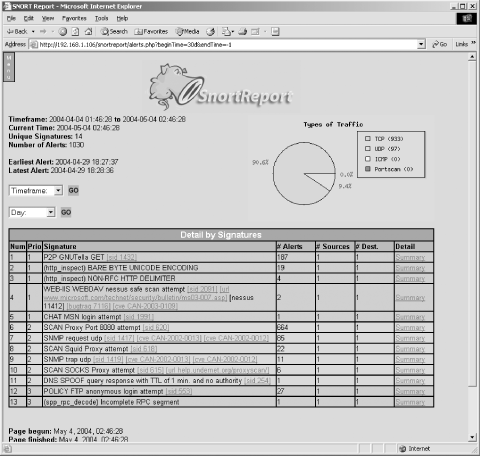 12.1.2 SnortSnarf
Installing SnortSnarf involves extracting the archive into a working directory. The entire program consists of a Perl script that parses the alert logfile generated by Snort (in /var/log/snort, by default) and generates a directory of summary web pages. Development of SnortSnarf also seems to be stalled. It's a very lightweight reporting tool that presents the user with a listing of alerts and links to summaries for the top 20 addresses (source and destination). SnortSnarf is not intended to be a monitoring interface for Snort, but simply a reporting tool. It pales in comparison to the alternatives. Figure 12-2 shows a sample SnortSnarf report page. Figure 12-2. SnortSnarf sample report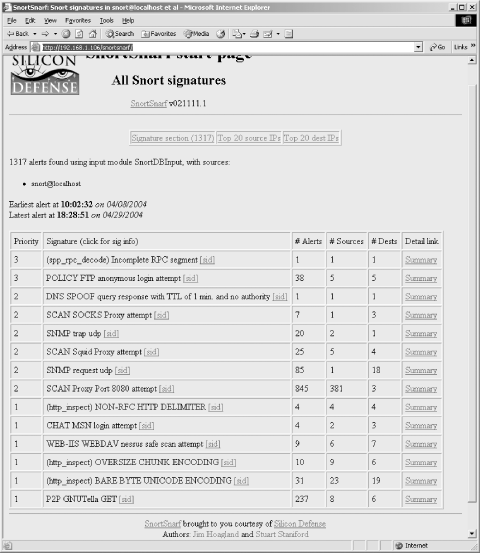 12.1.3 Cerebus
Download a precompiled executable for the operating system you will be using to run Cerebus. At the command line, supply the path to the Snort logfile (in unified binary output format) and the sid-msg.map file (included with the Snort rules download). Cerebus is a text-based console application; it's a fairly powerful utility for parsing Snort logfiles in the unified binary format. You can sort based on timestamp, address, alert priority, alert, or classification, and group and delete alerts by sorting criteria, as well. Cerebus is limited in that it can only read the unified binary Snort logs and thus is not a live monitoring tool. For environments that utilize the binary formatted logfiles, Cerebus can be useful for pruning alerts before sending the files to another tool, such as Barnyard (see Chapter 13). Figure 12-3 shows the Cerebus console interface. Figure 12-3. The Cerebus console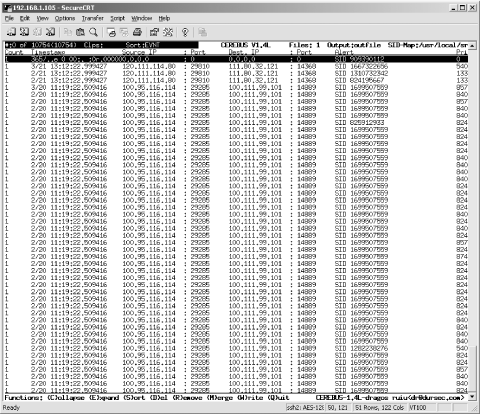 12.1.4 IDS Policy Manager
IDS Policy Manager comes in a standard Windows installer. It includes everything you need to manage Unix-based Snort sensors, including PuTTY's Secure Copy (SCP). IDS Policy Manager is a very full-featured application that allows you to manage multiple Unix-based Snort sensors. Interestingly, even though this application is Windows-based, you cannot use it to manage Windows-based Snort sensors. With the IDS Policy Manager interface, you can configure all aspects of Snort—variables, preprocessors, output plug-ins, and rules. The main sensor management interface is shown in Figure 12-4. Figure 12-4. The IDS Policy Manager sensor management interface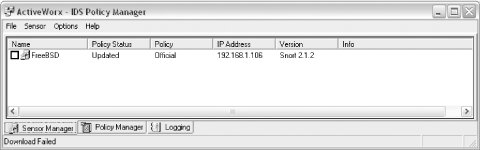 IDS Policy Manager keeps track of settings for a sensor (or group of sensors) by storing configuration information in the form of a policy that can be edited with the Policy Editor. Figure 12-5 shows the configuration screen for the flow preprocessors. Figure 12-5. The flow preprocessor configuration interface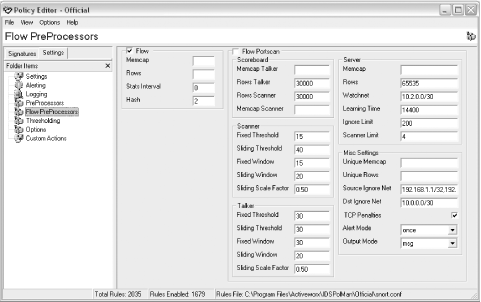 As mentioned, all aspects of Snort sensor configuration can be managed using the Policy Editor, including rules. Through this interface, it is possible to enable, disable, customize, merge, and delete rules. Figure 12-6 shows the interface to manage the active rules on the sensor. Figure 12-6. Managing the Snort rules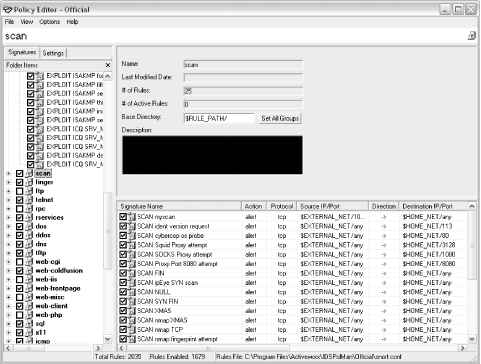 IDS Policy Manager is a very capable, powerful tool for managing multiple Snort sensors. Of all the open source tools, this is the most current in development. Its functionality rivals the commercial tools available for sensor management. 12.1.5 Oinkmaster
In order to install Oinkmaster, download and extract the archive, which contains a group of Perl scripts (there's also an RPM distribution). The most important of these is the one called Oinkmaster. The Oinkmaster.conf file stores configuration information. The file configures URLs to the latest Snort rules archives. Please note that the download paths have changed recently. You can download the latest set of rules for Snort Version 2.1.x from http://www.snort.org/dl/rules/snortrules-snapshot-2_1.tar.gz.The oinkmaster.conf file is also used to configure which files will not be compared and which rules will be disabled when the new rules are installed. Oinkmaster is run from the command line with a list of arguments (oinkmaster -h lists the options). Oinkmaster downloads the latest rule set, compares them to the existing set of rules, and updates the old rules, following the instructions in the configuration file. While Oinkmaster does a good job, it can cause problems if you let it update the rules automatically. To avoid problems, use the oinkmaster -c option, which performs a comparison and outputs it to the console. I normally use this mode to get a listing of what is new, changed, or deleted from the rule files. I then take this listing and use it as a guide when manually updating my rules. I have found Oinkmaster to be extremely useful in managing Snort rules. |
|
|
< Day Day Up > |
|