|
|
< Day Day Up > |
|
11.6 Managing TasksOne well-liked feature of SnortCenter is its ability to handle a wide assortment of tasks normally performed from the command line. A GUI interface via a web browser provides easy functionality for beginning users. However, SnortCenter still offers intermediate and advanced administrators the ability to perform complex tasks. This section covers some of the more complex options, along with command-line features for advanced users. 11.6.1 Updating Rules and SignaturesThere are various third-party scripts (Oinkmaster is one of the more well known) that assist in automating the download of the Snort rules database. They can all be obtained from the Snort page and installed and configured on most open source IDS machines. These and other scripts keep SnortCenter current with the latest signatures. In the event a new type of attack appears on the Internet, either download the latest rule set or manually add a new signature to the rulebase. Most administrators do not want to wait for the rules database to be automatically populated with the most recent releases. You know that adding a new rule is a simple matter when you use the SnortCenter management console. Open the Admin menu and select Import/Update Rules, then choose the option that works best for your needs. If you insist on using the command line, it is just as simple to place a rule within the snort.conf file and push the new configuration out to all sensors. For a local IDS, add the rule and restart the Snort process. Remember, the latest Snort signatures can be fetched from the main Snort download site at the following address: http://www.snort.org/dl/. 11.6.1.1 Automatic update featureFor those who prefer automatic updates to the signature database, an automatic update feature is included with the SnortCenter management console. This feature saves administrators the hassle of regularly downloading the rules and pushing them out to the sensors. SnortCenter can automatically grab the new rules at any given time—determined by a cron job—and push them out to the multiple sensors. First, verify that the following parameter is listed within the config.php file on the management console: $User_authentication = 2; If this variable is set to "0", user authentication is completely disabled. If it is set at "1", user authentication is enabled. When the variable is configured at "2", user authentication is disabled only for automatic update. Create a cron job on the management console similar to the following: 0 0 * * * curl "http://localhost/snortcenter/db_pars.php?source=net&push=yes" SnortCenter recommends the use of curl. There is no need to download another application for retrieving the latest ruleset. However, the wget utility can be used equally well as shown in the following example cron entry: 0 0 * * * wget -O - "http://localhost/snortcenter/db_pars.php?source=net&push=yes" This setting pushes out new updates to each of the sensors every night at midnight. It's as clever as it looks—you're not really using curl to download a file, you're using it to (effectively) click on a link through a cron job. 11.6.2 Managing False Positives and NegativesChapter 9 outlines several strategies to control the incidence of false positive and false negative alerts. SnortCenter provides a very useful interface for tuning and configuring your Snort environment as needed. To remove or disable rules generating false positives, locate the sid of the offending alert. The sid for a particular alert can be found in the sid-msg.map file or from the ACID web page. The Unique Alerts section helps find false positives or determine which rule generates the most alerts. If this alert is passive and can be safely turned off, find its sid and return to SnortCenter. Choose the Sensor Config button and go to the Rule Selection page. Figure 11-4 is an example page with all the rules deactivated. Figure 11-4. Deactivate rules that generate false positives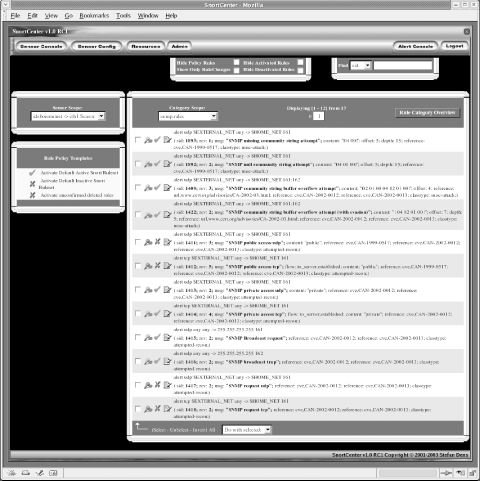 Under Category Scope, you can either choose the rules file you want to look in and locate the sid by hand or fill out the Find field in the upper right-hand box to locate the sid. To deactivate the rule associated to the sid, click on the pushpin icon. Take great care when disabling or altering rules. You can inadvertently rob the Snort installation of its effectiveness. 11.6.3 Editing Custom RulesThe concept of customizing rules to accommodate your unique network situation can also be applied to any existing rules. For example, to set up a custom rule to alert you in the event some user activates a peer to peer filesharing network and begins abusing network bandwidth by sharing illegal files, either adapt one of the existing rules that detects this traffic or customize a rule to detect a specific port number or signature. To create new rules most effectively, you can redefine existing rules and customize them to suit. For example, to capture new peer to peer filesharing traffic, first install the P2P program, capture sample traffic using tcpdump, and then look for identifying signatures or unique features within those packets. Using a sample rule from the p2p.rules file, create a new rule that contains a content string matching found in the captured packets. This new rule should alert you to traffic passed on your network using the peer to peer application. Some testing and tweaking of the content rule may be needed before false positives or negatives are eliminated. The ability to create and modify rules is a necessary skill for a security administator. You may not always be able to rely wholly on the Snort database. Your own internal network may deal with unique ports or applications that create false alerts. A brand new exploit may require you to create a rule to protect yourself before a rule is released on the Internet. SnortCenter can be invaluable in this process. |
|
|
< Day Day Up > |
|