|
|
< Day Day Up > |
|
Making Copies of Forensic EvidenceIf you have verified that your system has been attacked or exploited, the first thing to do is take immediate action to stop the attack or limit that machine's exposure. Ideally, this would mean disconnecting the machine from the network to conduct further analysis. If this is not possible, you will still want to disable any suspect accounts, kill any rogue processes, and possibly block offending IP addresses at the firewall while you figure out what is going on. Once you have eliminated the immediate danger, you should make a copy of any important data to look at offline per the tenet of good forensic analysis described earlier. You don't want to use your tools on live data. To do this, make a perfect copy of the data. This requires creating an image of the data rather than just copying it. You don't want to use the operating system's built-in copy functions because this might change file dates and insert other unwanted information. There are special tools for making these mirror-image copies. Unfortunately, there are not any good open source alternatives for the Windows platform right now (anyone want to sign up for a good Windows open source project?). The most popular program for Windows is Norton Ghost by Symantec, which retails for about $50.00. Under UNIX, there is an excellent open source program for doing this: dd, which stands for data dump.
You can use the dd tool to literally read blocks of data right off the hard disk and make exact copies of it. It goes directly to the media rather than using the file system, so it can capture deleted data and other things that a file system can't see. It can be used to make bit-wise copies of your data on a UNIX file system. Because UNIX treats devices as files, you can take a whole hard drive and replicate it this way by simply copying the device file with a tool like dd. Installing dd
Using ddThere are two ways to use dd. One way is to make a bit-wise copy, that is, copy the data bit by bit. This creates a mirror image of the data on another hard disk or partition. The other way is to create a single large file. This is sometimes convenient for analysis and portability purposes. You can easily make a hash of the file for verification purposes. This file is often referred to as an evidence file, and many forensic programs are designed to use these files as input. The basic format of the dd command is as follows: dd –if=input_file –of=output_file options where you replace input_file with the device file you want to copy, output_file with the filename you want to copy it to, and options with any dd options you want to use. The dd tool has many options, and Table 11.4 lists the basic ones.
So, if you want to copy the hard drive device /dev/hdc onto another hard drive, device hdd using dd, you could use the following command: dd –if=dev/hdc of=/dev/hdd bs=1024 conv=noerror,notrunc,sync This copies the contents of the device at /dev/hdc (probably your primary hard drive) to the device at /dev/hdd (probably your secondary hard drive). Make sure you understand which drives relate to which devices. As the sidebar on dd explains, a mistake here can be very costly!
If you want to create a single big evidence file instead, you can use the following command to copy the file onto a new device. dd if=/dev/hdc of=/mnt/storage/evidence.bin You will probably want to mount a new device to capture this file. It should preferably be brand new media so as not to taint the evidence with old data. Remember, even deleted data will show up with these tools. If you can't use fresh media, make sure it is truly wiped clean with a disk utility. The dd tool has this capability. Read the man pages for more information on this option. When you have all your evidence gathered, you are ready to analyze it further with a forensic toolkit. There are many excellent, professional-grade commercial toolkits. There are also some very good free toolkits available both for Windows and UNIX.
The Sleuth Kit by Brian Carrier is a compilation of various forensic tools that run under UNIX. It includes parts of the popular Coroner's Toolkit by Dan Farmer as well as other contributions, and works with the Autopsy Forensic Browser, which is a nifty Web interface for Sleuth Kit. It is designed to work with data files such as those output by disk utilities like dd. It is quite feature rich; in fact, it has more depth than some of the commercial programs available. Some of the key functions are:
Installing Sleuth Kit
Installing Autopsy Forensic BrowserThis program is the graphical interface counterpart to Sleuth Kit. Using it with Sleuth Kit will make your life a whole lot easier and allow you to produce some nice graphical output. You can still use the Sleuth Kit command line tools separately if you want to.
Using Sleuth Kit and Autopsy Forensic Browser
Creating and Logging Into a CaseThe Sleuth Kit with Autopsy Forensic Browser lets you monitor separate cases so you can track different incidents and customers. You will need to create a case for evidence files before you can work on them.
Adding a HostOnce you have logged into your case, you need to define at least one host that you are going to examine. This host represents the specific machine you are investigating.
Adding an ImageYou now need to add any data images for the hosts you have created. Use the copy of data you created using dd, Norton Ghost, or some other data replication utility.
Analyzing Your DataNow you are finally ready to begin your analysis. This may seem like a lot of setup work, but you will appreciate Sleuth Kit when you have a large number of images to manipulate or when you have to be able to produce a certain piece of data quickly. Go to the Image Gallery and click on the image you want to analyze. Table 11.5 lists the types of analysis you can perform on data images.
Figure 11.5. Results of Keyword Search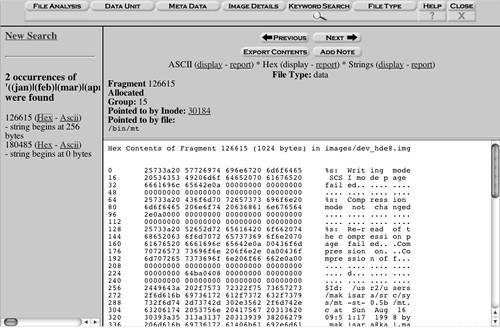 Sleuth Kit with Autopsy Forensic Browser gives you a powerful tool for organizing and analyzing forensic data that is on par with any professional lab in the country. This section has covered some of the basic functions, but whole books could be written about this great tool. Many commands and functions are not covered here. Read the online manual and other resources on the Web site for more details. The site also offers a monthly newsletter with interesting articles and tips for those in the forensic field.
The Forensic Toolkit is another great free program from the folks at Foundstone. This collection of tools can help you examine Window-based file systems and gather information for your forensic investigation. Version 1.4 of the program is fully open source licensed under the GPL. Version 2.0 is freeware and is usable for commercial purposes, but it has limitations on adding or changing the program and is not currently available in source form. Note that these tools work only on NTFS file systems. If you want to examine any FAT32 partitions, you will have to use different tools. Installing Forensic Toolkit
Using Forensic ToolkitThe tools consist of various command line utilities that generate various statistics and information on the file system in question. To execute a command, open up a command line window and type it (you must be in the appropriate directory). The following sections describe the individual tools. AfindThis utility searches for files by their access time. It does this without modifying any file access information, as the normal Windows utilities do. The basic format is:
afind search_directory options
where you replace search_directory with the directory to search and replace options with the appropriate search options. Table 11.6 lists the basic options.
HfindThis tool finds hidden files in the Windows operating system. It shows files that have the hidden attribute bit turned on and those hidden using the Windows NT special directory/system attribute method. The format is:
hfind path
where path is replaced with the path you want to search. It lists the hidden files and their last date and time of access. Be careful of searching the whole hard drive as this could take a while. SfindThis tool finds hidden datastreams on the hard disk. These are different from hidden files in that they won't be seen on the hard disk when you click on the option to view hidden files. Hidden datastreams are an NTFS feature that allows certain programs to access alternate datastreams. The files are linked to a parent file, which is visible, but may not be deleted when the file system deletes the parent file. They may be used to hide data or malware. The format of the sfind command is:
sfind path
where path is the path you want to search. Again, this may take quite some time if you are searching the root directory of a large drive. FileStatThis command creates a full listing of file attributes, including security information. It only works on one file at a time. You can pipe the output into a text file for further processing. This command generates quite a lot of information, including a lot of file descriptor information you don't normally see. Listing 11.5 shows a sample of this information for a file called test.txt. Listing 11.5. FileStat Output
Creation Time - 01/10/2004 03:18:40
Last Mod Time - 01/10/2004 03:18:40
Last Access Time - 01/10/2004 03:18:40
Main File Size - 11
File Attrib Mask - Arch
Dump complete...Dumping C:\temp\test.txt...
SD is valid.
SD is 188 bytes long.
SD revision is 1 == SECURITY_DESCRIPTOR_REVISION1
SD's Owner is Not NULL
SD's Owner-Defaulted flag is FALSE
SID = TONYVPRDESKTOP/Tony Howlett S-1-5-21--181663460ó
SD's Group-Defaulted flag is FALSE
SID = TONYVPRDESKTOP/None S-1-5-21--181663460--953405037-
SD's DACL is Present
SD's DACL-Defaulted flag is FALSE
ACL has 4 ACE(s), 112 bytes used, 0 bytes free
ACL revision is 2 == ACL_REVISION2
SID = BUILTIN/Administrators S-1-5-32-544
ACE 0 is an ACCESS_ALLOWED_ACE_TYPE
ACE 0 size = 24
ACE 0 flags = 0x00
ACE 0 mask = 0x001f01ff -R -W -X -D -DEL_CHILD
-CHANGE_PERMS -TAKE_OWN
SID = NT AUTHORITY/SYSTEM S-1-5-18
ACE 1 is an ACCESS_ALLOWED_ACE_TYPE
ACE 1 size = 20
ACE 1 flags = 0x00
ACE 1 mask = 0x001f01ff -R -W -X -D -DEL_CHILD -CHANGE_PERMS -TAKE_OWN
SID = TONYVPRDESKTOP/Tony Howlett S-1-5-21--181663460-
ACE 2 is an ACCESS_ALLOWED_ACE_TYPE
ACE 2 size = 36
ACE 2 flags = 0x00
ACE 2 mask = 0x001f01ff -R -W -X -D -DEL_CHILD -CHANGE_PERMS -TAKE_OWN
SID = BUILTIN/Users S-1-5-32-545
ACE 3 is an ACCESS_ALLOWED_ACE_TYPE
ACE 3 size = 24
ACE 3 flags = 0x00
ACE 3 mask = 0x001200a9 -R -X
SD's SACL is Not Present
Stream 1:
Type: Security
Stream name = ??? ? Size: 188
Stream 2:
Type: Data
Stream name = ??? ? Size: 11
Stream 3:
Type: Unknown
Stream name = ??? ? Size: 64
HuntThis tool can be used to generate a lot of information on a system using the Windows NULL session capabilities. Depending on the permissiveness of your system, it could generate significant information such as users lists, shares, and services running. The command takes the following format:
hunt system_name
where system_name represents the proper Windows host name of the system you want to run hunt on. Listing 11.6 represents an example of this output. Listing 11.6. Hunt Outputshare = IPC$ - Remote IPC share = print$ - Printer Drivers share = SharedDocs - share = Printer3 - Acrobat Distiller share = Printer2 - Acrobat PDFWriter User = Administrator, , , Built-in account for administering the computer/domain Admin is TONYVPRDESKTOP\Administrator User = Howlett, , , User = Guest, , , Built-in account for guest access to the computer/domain User = HelpAssistant, Remote Desktop Help Assistant Account, Account for Providing Remote Assistance User = SUPPORT_388945a0, CN=Microsoft Corporation,L=Redmond,S=Washington,C=US, , This is a vendor's account for the Help and Support Service User = Tony Howlett, In this listing you can see two users you don't normally see in the User Accounts section on your Windows system: the HelpAssistant and SUPPORT users. These are system-level users for internal programs (the Remote assistance features and the annoying Notify Support feature that pops up every time a program bombs out). Other hidden users concealed by a skilled intruder could be revealed using this tool. This chapter is not meant to be a comprehensive listing of all possible forensic tools, but these tools should give you enough to get started with basic forensic activity on just about any system. If you are doing this as a career or have an involved investigation, there are many other tools available. For a good listing of open source forensic tools, visit www.opensourceforensics.org/. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|
< Day Day Up > |
|