No matter how complex the firewall is, in its most simple form, a firewall allows and disallows access to specific services based on host addresses, networks, or other such trigger criteria. The services, ports, and daemon names (for Red Hat/Fedora Core systems) that most Linux sys-admins are concerned about are shown in Table 11-1.
|
Service Name |
Port |
Description |
Red Hat/Fedora Daemon Name |
|---|---|---|---|
|
Ftp |
21 |
VS-FTP |
Vsftpd |
|
Ssh |
22 |
OpenSSH/sftp/scp |
Sshd |
|
Http |
80 |
Apache/Web |
Httpd |
|
Sunrpc |
111 |
RPC/NFS related service |
Portmap |
|
Https |
443 |
Apache/web SSL |
Httpd |
|
Smtp |
25 |
Sendmail/SMTP mail |
Sendmail |
|
Domain |
53 |
BIND DNS |
Named |
|
Ipp |
631 |
CUPS |
Cupsd |
|
Nfs |
2049 |
Network file system |
nfs |
|
Mysql |
3306 |
MySQL database |
mysqld |
You'll need to know these service names and ports whether you're controlling access to them on a single stand-alone server firewall or protecting an entire network of these services as a NAT router firewall setup would do.
Lets take a look at when you might want to just use basic service access control on a single server with TCP wrappers.
If the services that you want to allow or disallow access to are running on a server connected to a trusted network or LAN, you can use either TCP wrappers or iptables to set up your local server-side service access control (personal firewall). That said, TCP wrappers is really not considered to be a true hardened firewall grade form of access control because incoming data is allowed past the networking stack into what's called user space. This is where many Internet worms and attacks are launched to strike, and this in turn means that you can still be cracked if your TCP wrappers-based system is attacked with a known TCP wrappers exploit. Armed with this knowledge, if you have a single server on an untrusted network or directly on the Internet and you wish to run a serious single host-based firewall configuration, iptables should be your only real choice for a real firewall.
If you're already on a secure network and you just want to allow/disallow services to various IP addresses, hosts, or networks within your network, then TCP wrappers might be easier for you to use.
| Caution |
While TCP wrappers is fine for doing basic allow/deny access to services on a trusted network or LAN, it should not be used in the wild, on an untrusted network, or on the Internet without some form of real firewall in front of it (such as iptables or a full-blown network firewall). |
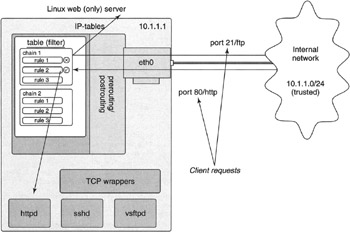
Figure 11-1 shows a basic single-homed or stand-alone firewall. Note the single computer with its single network connection. This would typically be the configuration of a server running its own iptables-based firewall or TCP wrappers service control, already behind a network-wide corporate firewall, for example.
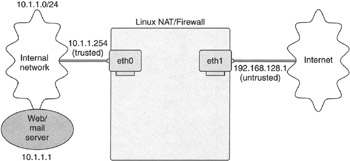
Dual-homed firewalls (Figure 11-2) are designed to protect an entire network of PCs or servers, and sometimes act as NAT-based routers for your LAN (more on this later). See Figure 11-2 for an example of a dual-homed firewall or network firewall configuration.
| Note |
In addition to single-homed and dual-homed firewalls, you may also run across tri-homed firewalls. These firewalls incorporate a DMZ, or demilitarized zone, which is a semiprotected network outside the protected internal network. Tri-homed firewalls are beyond the scope of this book, but you can learn more by consulting RFC 2647 or doing a Google web search on firewall and DMZ. |
As you read more about firewalls, you will come across the terms trusted and untrusted interfaces. These terms are used in relation to network and security boundaries. A dual-homed (or two network card) firewall is usually placed between a trusted and an untrusted network, and so the two interfaces on the firewall that physically connect to these networks get their names accordingly. If you have a trusted network interface (for example, eth0) and an untrusted network interface (such as eth1), you need to use iptables (along with ip forwarding) to control network access through your firewall from one interface to the other. (You can see the interfaces and the networks they're connected to in Figure 11-2.)
Now that some of the basics on firewall theory are out of the way, the next section focuses on the differences between TCP wrappers and iptables, and when and how to use each.