A.5. Web Application Security ToolsWeb security tools provide four types of functionality, and there is a growing trend to integrate all the types into a single package. The four different types are:
Many free (and some open source) web security tools are available:
These tools are rich in functionality but lacking in documentation and quality control. Some functions in their user interfaces can be less than obvious (this is not to say commercial tools are always user friendly), so expect to spend some time figuring out how they work. The trend is to use Java on the client side, making the tools work on most desktop platforms. Paros and WebScarab compete for the title of the most useful and complete free tool. The Burp tools show potential, but lack integration and polish. A.5.1. ParosParos (see Figure A-9) will probably fill most of your web security assessment needs. It can be used to do the following:
Figure A-9. Paros allows for web site visualization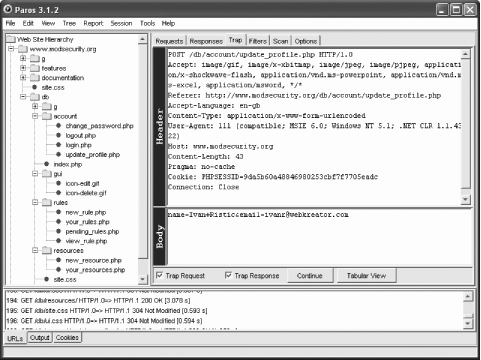 A.5.2. Commercial Web Security ToolsIf you are more interested in commercial tools than in open source ones, many are available. Categorizing them is sometimes difficult because they often include all features of interest to web security professionals in one single package. Most tools are a combination of scanner and proxy, with a bunch of utilities thrown in. So, unlike the open source tools where you have to use many applications from different authors, with a commercial tool you are likely to find all you need in one place. Commercial web security tools offer many benefits:
One significant disadvantage is the cost. The area of web application security is still very young, so it is natural that tools are expensive. From looking at the benefits above, employees of larger companies and web security consultants are the most likely to buy commercial tools. Members of these groups are faced with the unknown, have limited time available, and must present themselves well. An expensive commercial tool often increases a consultant's credibility in the eyes of a client. Here are some of the well-known commercial tools:
|